You can now replace your background with an image in Google Meet. You can either use Google’s hand-picked images, which include office spaces, landscapes, and abstract backgrounds, or upload your own image.
Saturday, October 31, 2020
Replace your background in Google Meet
Thursday, October 22, 2020
Introducing data protection insights reports
What’s changing
- How many files in your organization contain sensitive information.
- How many sensitive files in your organization have been shared externally.
- Insights into the type of sensitive information (e.g. credit card numbers, social security numbers, etc.) in those files.
Who’s impacted
Why it matters
Getting started
- Admins:
- Reports will be produced periodically. When they’re created, links to the report will be sent by email, and an alert will be shown in the Admin console. You can also find the report in the Admin console at Security > Data protection.
- Reports will only be accessible by super admins and other admins with the View DLP rule privilege.
- You can turn off the report by going to Admin console > Data Protection > Data protection insights.
- Visit our Help Center to learn more about managing DLP insights reports.
- End users: No end user impact.
Wednesday, October 21, 2020
Windows 10 20H2 is released, here are the new features

Microsoft is rolling out the next version of Windows 10 called "20H2" and the update is available for those who manually check for updates using the Settings app.
20H2 Update is not a huge release and it does not bring a major overall to key features of Windows 10, but Microsoft says this update comes with a lot of improvements that should improve overall user experience.
Microsoft is rolling out the feature update via an enablement package that allows you to update your system very quickly with a single reboot.
The features of Windows 10 version 20H2 are already included in Windows 10 May 2020 Update and enablement package is a "master switch" that would simply turn on dormant features, such as the new Start Menu.
To get the update via enablement package, Microsoft says users should be using at least the September 2020 cumulative updates. Once you've installed the cumulative updates, simply head to Settings > Update & Security and begin the download by clicking 'Download & install now" button.
Here's a list of all some noticeable new features in this feature update
Theme-aware Start Menu
This feature update will ditch the colored backgrounds live tiles in the Start Menu for partially transparent theme-aware tiles. These new tiles are supposed to match the look and feel of the new Fluent Design system.
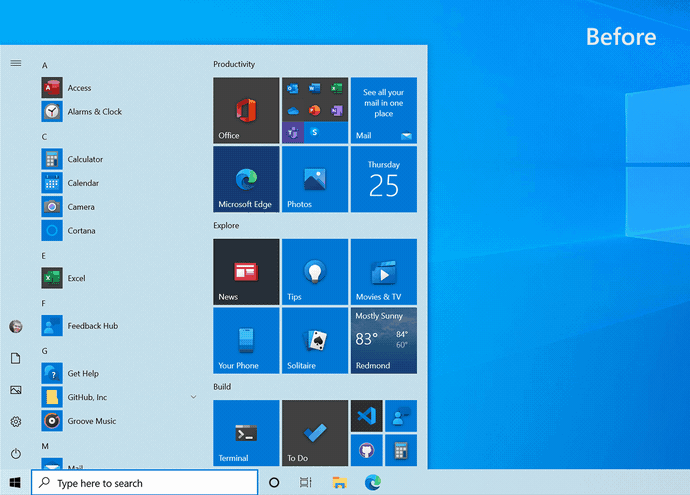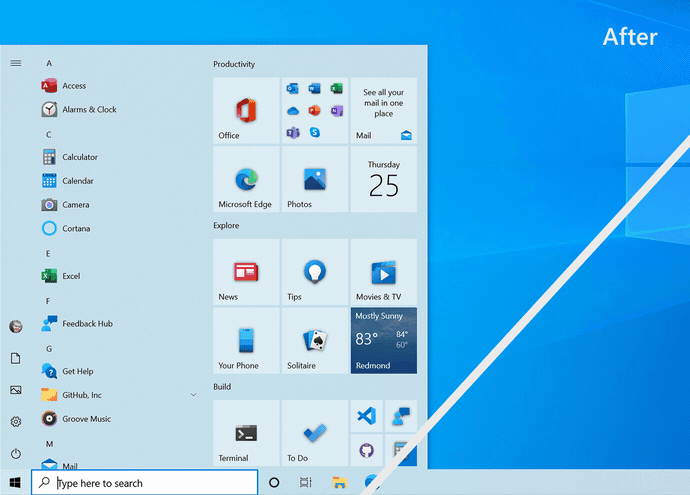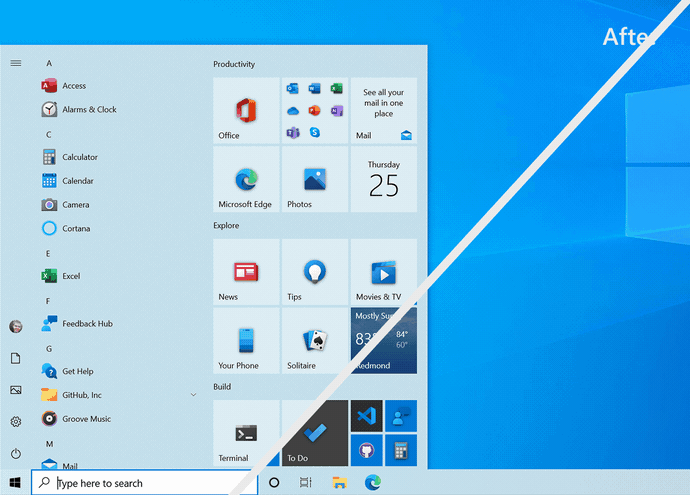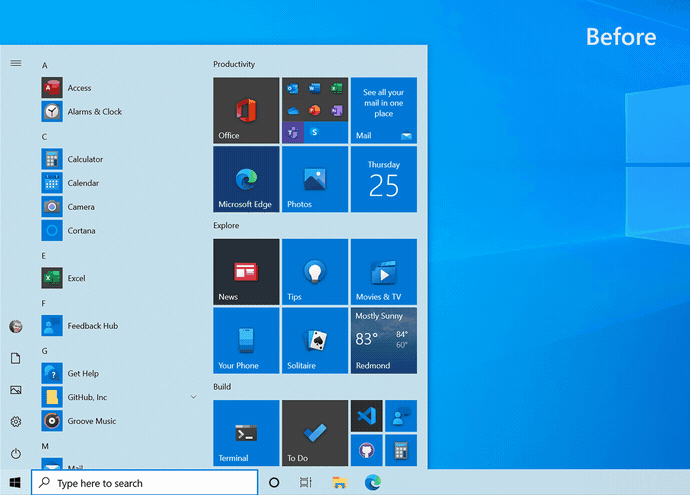
"We are freshening up the Start menu with a more streamlined design that removes the solid color backplates behind the logos in the apps list and applies a uniform, partially transparent background to the tiles," Microsoft said.
Microsoft Edge (Chromium) is now built-in
Microsoft Chromium edge is now the default web browser on Windows 10 and it replaces the classic UWP Edge. Chromium Edge will be pre-installed on all devices that will ship with October update or newer.
Alt + Tab improvements
In May 2020 Update or older, Alt + Tab app switcher of Windows 10 allows you to switch between the open windows of your apps (UWP or Win32), but after the October Update, Microsoft says it will show your Edge tabs right alongside the app windows.
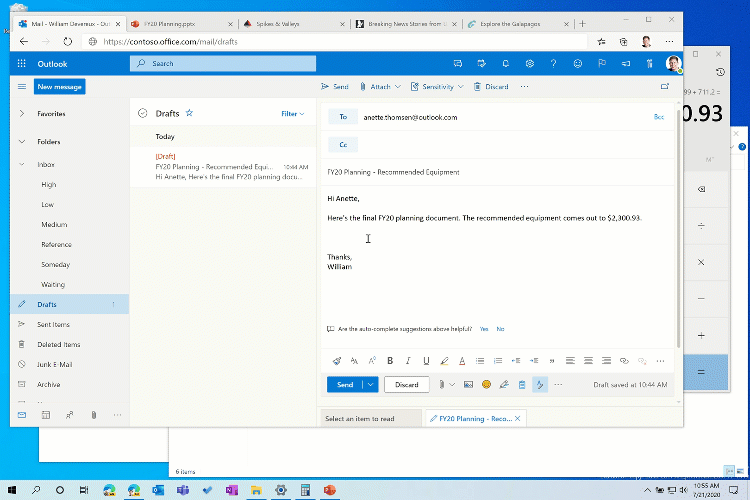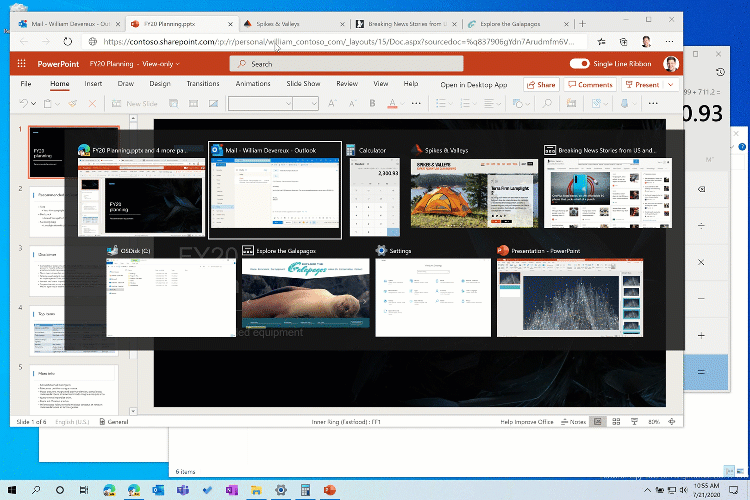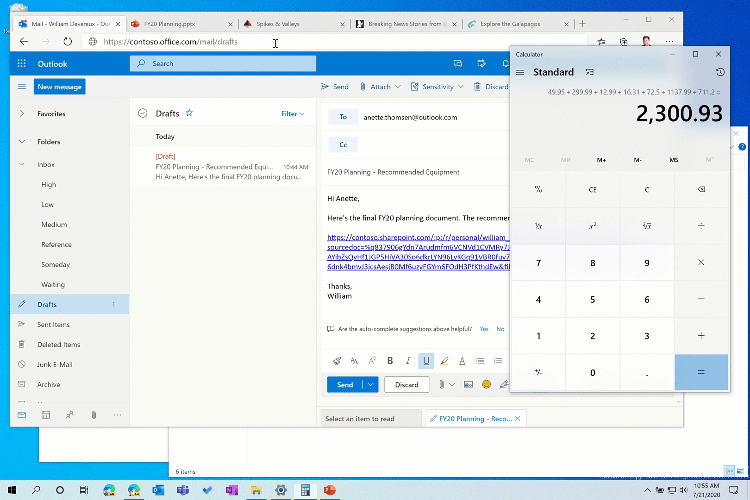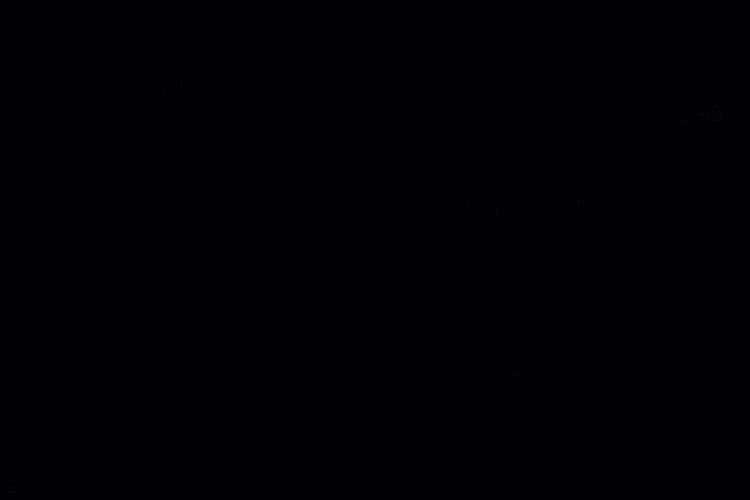
This feature is supposed to make switching between open tabs as seamless as switching between open windows.
System settings About page is getting better
In 20H2 update, all your information found in Control Panel’s System applet will be migrated into the 'About' Settings page under Settings > System > About.
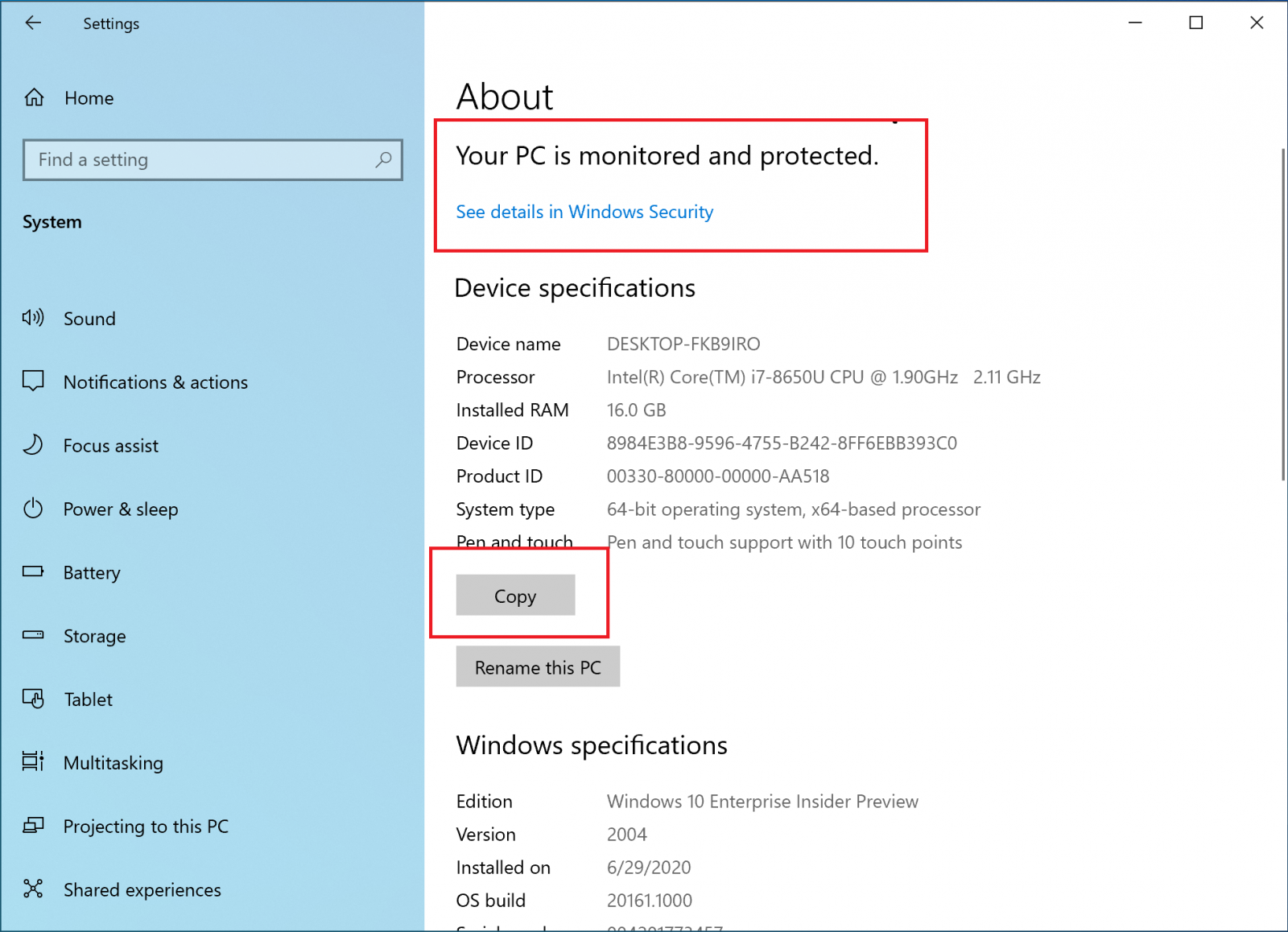
This new About page now allows you to copy your system information to the clipboard, which means that you can now easily share your information with Microsoft tech support for debugging.
Other improvements
- Tablet experience for 2-in-1 devices: When you detach the keyboard on Surface Book-like devices, Microsoft's notification toast asking you to switch to tablet mode will no longer appear.
- Refresh rate: You can now change your display refresh rate from Settings > System > Display > Advanced display settings.
- Modern Device Management (MDM) improvements
Friday, October 16, 2020
Introducing .NET Live TV – Daily Developer Live Streams
Today, James accounce launching .NET Live TV, your one stop shop for all .NET and Visual Studio live streams across Twitch and YouTube. We are always looking for new ways to bring great content to the developer community and innovate in ways to interact with you in real-time. Live streaming gives us the opportunity to deliver more content where everyone can ask questions and interact with the product teams.
We started our journey several years ago with the .NET Community Standup series. It’s a weekly “behind the scenes” live stream that shows you what goes into building the runtimes, languages, frameworks, and tools we all love. As it grew, so did our dreams of delivering even more awesome .NET live stream content.
.NET Live TV takes things to a whole new level with the introduction of new shows and a new website. It is a single place to bookmark so you can stay up to date with live streams across several Twitch and YouTube channels and with a single click can join in the conversation.
Windows 10 Settings gets a modern Disk Management tool
Microsoft continues to migrate legacy Windows tools into modern versions found in the Windows 10 settings with the introduction of a new Disk Management tool.
Since Microsoft introduced its modern Settings interface in Windows 8, users have been left with a confusing mess of how to configure Windows settings.
Do they use the new modern Windows settings interface, old legacy tools, or the Control Panel to customize the operating system?
In July, Microsoft announced that they were migrating the widely-used System control panel into the modern Windows 10 About settings page.
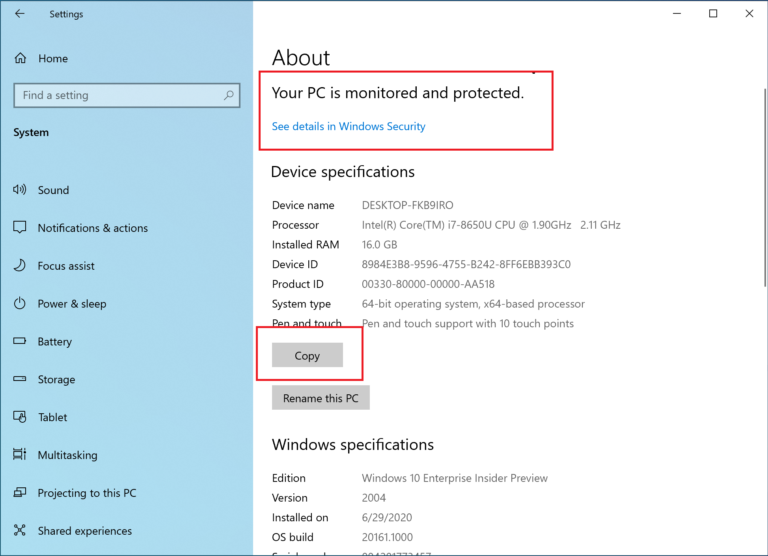
Microsoft has also started testing redirecting Windows 10 users who opened the older System control panel to this new About page.
To BleepingComputer, this indicated that Microsoft ultimately wants to do away with the old legacy controls in the Control Panel and eventually move everything to the new modern Settings interface.
Windows 10 Settings gets a modern Disk Management tool
Since at least Windows 95, if not older, users have had access to the standalone Disk Management tool (diskmgmt.msc) that is used to manage the storage devices used by Windows.
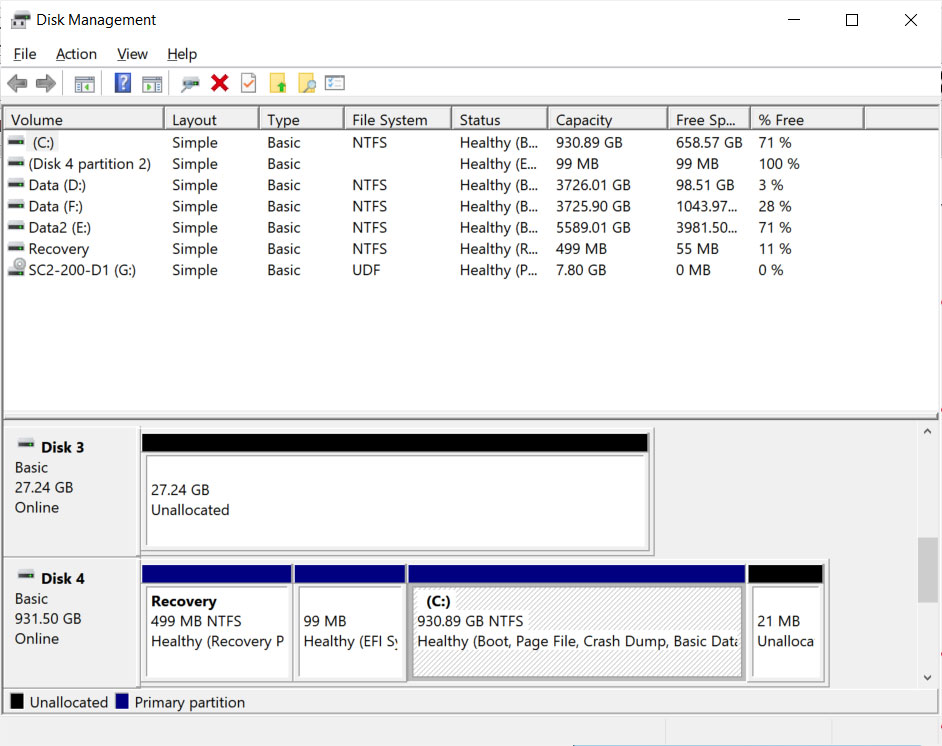
With today's release of Windows 10 Insider build 20197, Microsoft has now introduced a modern 'Manage Disks and Volumes' utility that has better integration with the Storage Spaces and Storage settings.
This new tool allows Windows users to view disk information, create and format volumes, and assign drive letters.
To access this new tool, you would go to Settings > System > Storage and click on Manage Disks and Volumes.
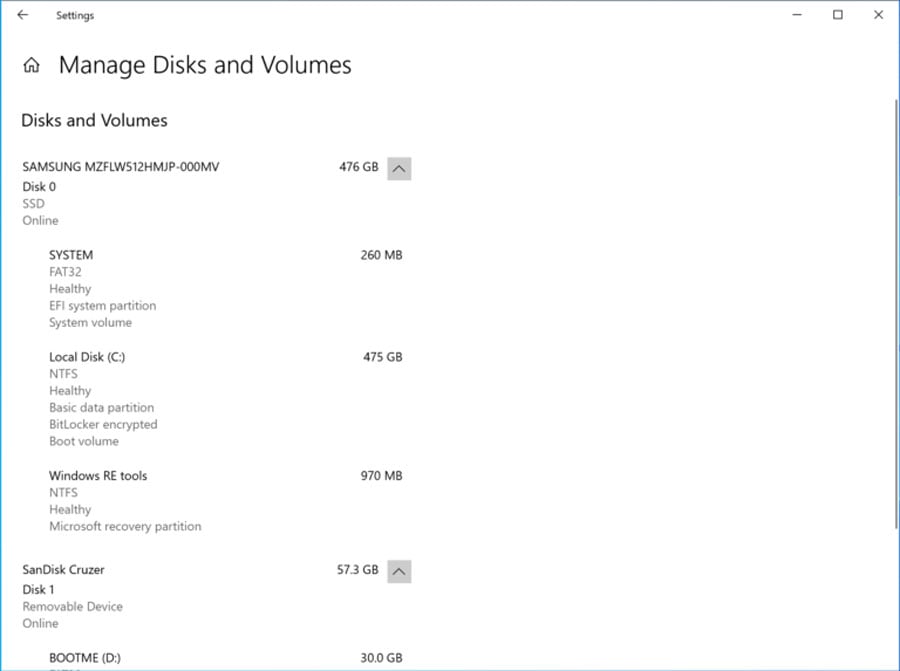
Microsoft has stated that this not currently replacing the existing Disk Management MMC tool, and Windows users can still use it if they wish.
How to Download the Windows 10 1909 ISO From Microsoft
Now that Microsoft has released Windows 10 1909, otherwise known as the November 2019 Update, ISO disk images for this new version are also available. As it is always a good practice to have the original media for the latest version of Windows 10 available, we will explain how you can download the Windows 10 1909 ISO directly from Microsoft.
For those nor familiar with an ISO, it is sector-by-sector copy of a DVD that is stored in a disk image file. This ISO file can then be written, or burned, to another DVD to create a replica of the original, mounted as a drive letter in Windows, or extracted by a program like 7-Zip to access the files contained in it.
While the Windows 10 Media Creation Tool can be used to create Windows 10 media, this media is meant to be used to upgrade your PC and is customized towards that goal. A Windows 10 ISO, though, is the original media that can be used to install a variety of different versions of Windows 10 depending on your license.
Unfortunately, Microsoft does not normally offer a Windows 10 ISO, but using a trick you can still get it directly from Microsoft's site as explained below.
How to download a Windows 10 1909 ISO
Normally when you go to Microsoft's "Download Windows 10" page, you are only given the option to update via Windows Update or to download the Windows 10 Media Creation Tool.
Below we are going to explain a method that causes Microsoft to offer an ISO image file for Windows 10 1909 instead.
To download the Windows 10 1909 ISO, follow these steps:
- Go to Windows 10 download page in Chrome or the new Microsoft Edge.
- Click on the Chrome menu, then More Tools, and then select Developer tools as shown below.
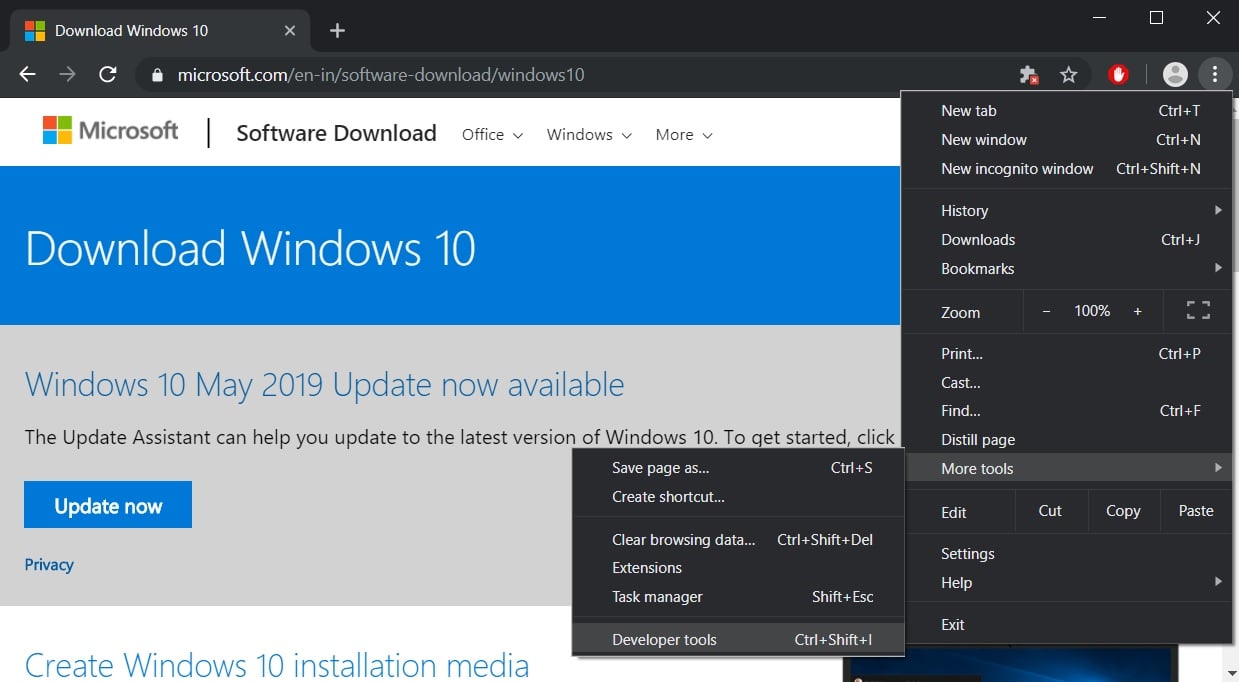
- Now press Ctrl + Shift + M to open the Device toolbar. This toolbar lets you force Chrome to impersonate another device such as a mobile phone or a tablet.
Click on the menu that should show Responsive and select iPad or iPad Pro so that you have a larger screen to work with.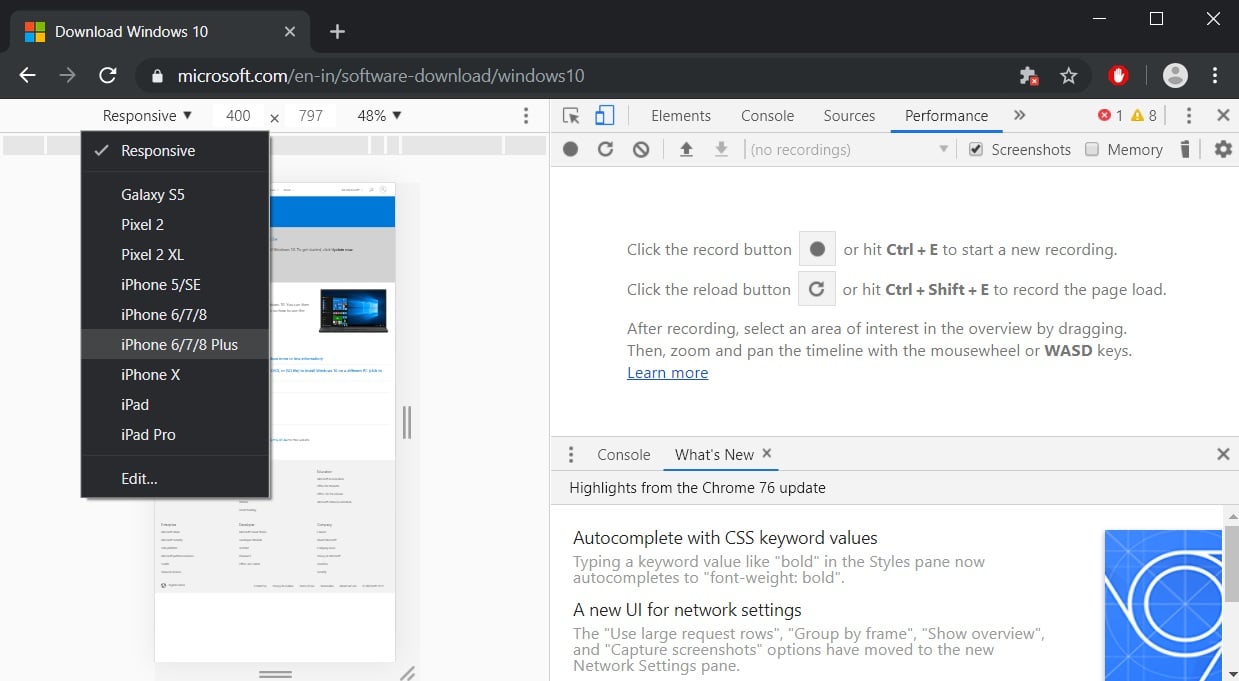
- When you select one of these devices, you should see the screen resize to reflect the size of the devices screen. At this point, I suggest you change the zoom to 100% as shown below.
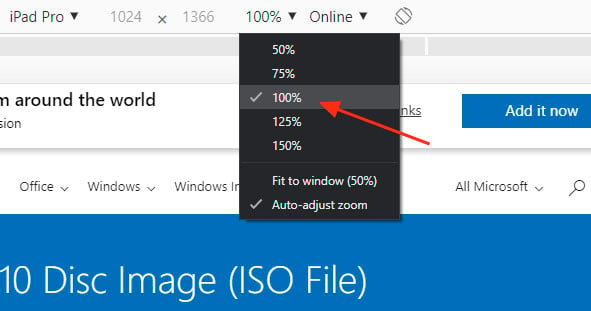
- Now refresh the page in the browser by pressing the F5 key. Once the page refreshes, Microsoft's site will now offer you the Windows 10 ISO instead of the Media Creation Tool as seen below.
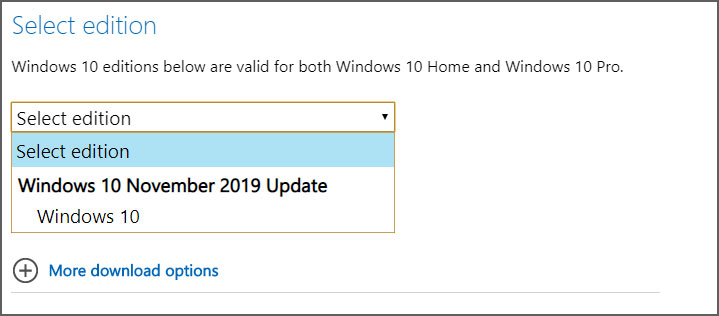
- Select the Windows 10 option under "Windows 10 November 2019 Update" and then select Confirm.
- After a few seconds, Microsoft's site will now ask you to select the language for your ISO.
Select your language and press the Confirm button again.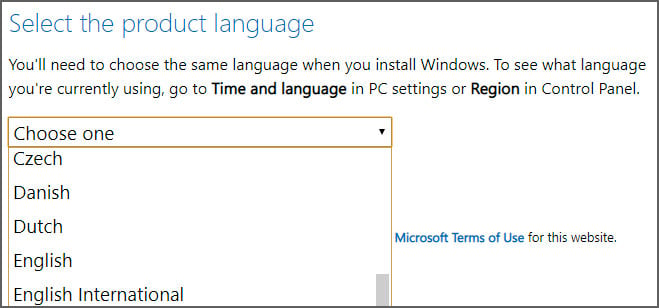
- Finally, you will be asked to either download the 32-bit or 64-bit ISO. When ready, click on one of these choices and the respective Windows 1909 ISO image will be downloaded.
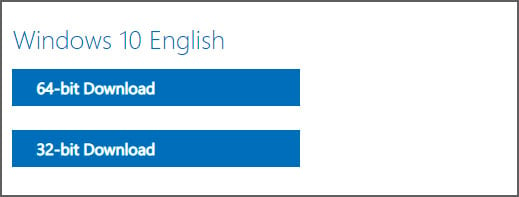
It should be noted that the above instructions work in any Chromium-based browser, not only Chrome or the new Edge.
What should you do with the ISO?
Now that you have downloaded the Windows 10 1909 ISO, you may be wondering what you should do with it.
As blank writable DVDs are fairly cheap, costing between $0.50 or $0.70 at Amazon when you buy them in a multi-pack, my suggestion is to burn the ISO onto a DVD and store it in a safe place. This way you have it available in case you need to use it in the future as an emergency repair disk or as Windows installation media.
For example, if your computer is no longer able to boot due to an infection that disables the Windows 10 recovery environment, you can boot your computer using the Windows 10 installation media to repair your computer.
As Microsoft releases new feature updates at least twice per year, it is suggested that you create new ISOs each time a new Windows 10 feature update is released.
Office 365 adds protection against downgrade and MITM attacks
Microsoft is working on adding SMTP MTA Strict Transport Security (MTA-STS) support to Exchange Online to ensure Office 365 customers' email communication security and integrity.
Once MTA-STS is available in Office 365 Exchange Online, emails sent by users via Exchange Online will only one delivered using connections with both authentication and encryption, protecting against both email interception and attacks.
Protection against MITM and downgrade attacks
MTA-STS strengthens Exchange Online email security and solves multiple SMTP security problems including the lack of support for secure protocols, expired TLS certificates, and certs not issued by trusted third parties or matching server domain names.
Given that mail servers will still deliver emails even though a properly secured TLS connection can’t be created, SMTP connections are exposed to various attacks including downgrade and man-in-the-middle attacks.
"[D]owngrade attacks are possible where the STARTTLS response can be deleted, thus rendering the message in clear text," Microsoft says. "Man-in-the-middle (MITM) attacks are also possible, whereby the message can be rerouted to an attacker’s server."
"MTA-STS (RFC8461) helps thwart such attacks by providing a mechanism for setting domain policies that specify whether the receiving domain supports TLS and what to do when TLS can’t be negotiated, for example stop the transmission," the company explains in a Microsoft 365 roadmap entry.
"Exchange Online (EXO) outbound mail flow now supports MTA-STS," Microsoft also adds.
Exchange Online SMTP MTA Strict Transport Security (MTA-STS) support is currently in development and the company is planning to make it generally available during December in all environments, for all Exchange Online users.
DNSSEC and DANE for SMTP also coming
Microsoft is also working on including support for the DNSSEC (Domain Name System Security Extensions) and DANE for SMTP (DNS-based Authentication of Named Entities) to Office 365 Exchange Online.
Support for the two SMTP standards will be added to both inbound and outbound mail, "specific to SMTP traffic between SMTP gateways" according to the Microsoft 365 roadmap [1, 2] and this blog post.
According to Microsoft, after including support for the two SMTP security standards in Exchange Online:
- DANE for SMTP will provide a more secure method for email transport. DANE uses the presence of DNS TLSA resource records to securely signal TLS support to ensure sending servers can successfully authenticate legitimate receiving email servers. This makes the secure connection resistant to downgrade and MITM attacks.
- DNSSEC works by digitally signing records for DNS lookup using public key cryptography. This ensures that the received DNS records have not been tampered with and are authentic.
Microsoft October 2020 Patch Tuesday fixes 87 security bugs
Today is Microsoft's October 2020 Patch Tuesday, and your Windows administrators will be pulling their hair out as they install new updates and try to fix bugs that pop up.
With the October 2020 Patch Tuesday security updates release, Microsoft has released fixes for 87 vulnerabilities in Microsoft products and an advisory about today's Adobe Flash Player update.
Of the 87 vulnerabilities fixed today, 12 are classified as Critical, and 74 are classified as Important, and one as moderate.
For information about the non-security Windows updates, you can read about today's Windows 10 KB4579311 & KB4577671 Cumulative Updates.
Publicly disclosed vulnerabilities:
This month's Patch Tuesday security updates include a whopping six publicly disclosed vulnerabilities. The good news is that Microsoft states that none of them have been seen publicly exploited.
One of the vulnerabilities, CVE-2020-16938, was found by security researcher Jonas L, who recently began disclosing vulnerabilities on Twitter after being frustrated by Microsoft's bounty program.
- CVE-2020-16938 - Windows Kernel Information Disclosure Vulnerability
- CVE-2020-16885 - Windows Storage VSP Driver Elevation of Privilege Vulnerability
- CVE-2020-16901 - Windows Kernel Information Disclosure Vulnerability
- CVE-2020-16908 - Windows Setup Elevation of Privilege Vulnerability
- CVE-2020-16909 - Windows Error Reporting Elevation of Privilege Vulnerability
- CVE-2020-16937 - .NET Framework Information Disclosure Vulnerability
Microsoft has not disclosed who found the other five vulnerabilities.
Vulnerabilities of interest
While there were no zero-days this month, there were quite a few interesting vulnerabilities that can be exploited remotely.
Below are the more interesting Critical security vulnerabilities fixed today:
- "CVE-2020-16911 - GDI+ Remote Code Execution Vulnerability" lets attackers create specialty crafted websites that can execute commands with elevated privileges on the visitor's computer.
- "CVE-2020-16947 - Microsoft Outlook Remote Code Execution Vulnerability" allows attackers to send specially crafted emails that can execute commands when opened in the Microsoft Outlook software. This attack also works when an email is viewed in the preview pane.
- "CVE-2020-16898 - Windows TCP/IP Remote Code Execution Vulnerability" can be exploited by sending specially crafted ICMPv6 Router Advertisement packets to a remote Windows computer. If successful, it could allow a remote attacker to execute commands on the targeted computer.
- "CVE-2020-16891 - Windows Hyper-V Remote Code Execution Vulnerability" would allow an attacker, or malware, on a guest Hyper-V virtual machine to execute commands on the host operating system.
- "CVE-2020-16915 - Media Foundation Memory Corruption Vulnerability" can be exploited for remote code execution by tricking a user into visiting a malicious website.
Recent security updates from other companies
Other vendors who released security updates in October include:
- Adobe released security updates today for Adobe Flash Player.
- Apple released security updates for macOS, tvOS, and watchOS.
- Intel released its October 2020 platform update.
- SAP released its October 2020 security updates today.
The October 2020 Patch Tuesday Security Updates
Below is the full list of resolved vulnerabilities and released advisories in the October 2020 Patch Tuesday updates. To access the full description of each vulnerability and the systems that it affects, you can view the full report here.
| Tag | CVE ID | CVE Title | Severity |
|---|---|---|---|
| .NET Framework | CVE-2020-16937 | .NET Framework Information Disclosure Vulnerability | Important |
| Adobe Flash Player | ADV200012 | October 2020 Adobe Flash Security Update | Critical |
| Azure | CVE-2020-16995 | Network Watcher Agent Virtual Machine Extension for Linux Elevation of Privilege Vulnerability | Important |
| Azure | CVE-2020-16904 | Azure Functions Elevation of Privilege Vulnerability | Important |
| Group Policy | CVE-2020-16939 | Group Policy Elevation of Privilege Vulnerability | Important |
| Microsoft Dynamics | CVE-2020-16978 | Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability | Important |
| Microsoft Dynamics | CVE-2020-16956 | Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability | Important |
| Microsoft Dynamics | CVE-2020-16943 | Dynamics 365 Commerce Elevation of Privilege Vulnerability | Important |
| Microsoft Exchange Server | CVE-2020-16969 | Microsoft Exchange Information Disclosure Vulnerability | Important |
| Microsoft Graphics Component | CVE-2020-16911 | GDI+ Remote Code Execution Vulnerability | Critical |
| Microsoft Graphics Component | CVE-2020-16914 | Windows GDI+ Information Disclosure Vulnerability | Important |
| Microsoft Graphics Component | CVE-2020-16923 | Microsoft Graphics Components Remote Code Execution Vulnerability | Critical |
| Microsoft Graphics Component | CVE-2020-1167 | Microsoft Graphics Components Remote Code Execution Vulnerability | Important |
| Microsoft NTFS | CVE-2020-16938 | Windows Kernel Information Disclosure Vulnerability | Important |
| Microsoft Office | CVE-2020-16933 | Microsoft Word Security Feature Bypass Vulnerability | Important |
| Microsoft Office | CVE-2020-16929 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office | CVE-2020-16934 | Microsoft Office Click-to-Run Elevation of Privilege Vulnerability | Important |
| Microsoft Office | CVE-2020-16932 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office | CVE-2020-16930 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office | CVE-2020-16955 | Microsoft Office Click-to-Run Elevation of Privilege Vulnerability | Important |
| Microsoft Office | CVE-2020-16928 | Microsoft Office Click-to-Run Elevation of Privilege Vulnerability | Important |
| Microsoft Office | CVE-2020-16957 | Microsoft Office Access Connectivity Engine Remote Code Execution Vulnerability | Important |
| Microsoft Office | CVE-2020-16918 | Base3D Remote Code Execution Vulnerability | Important |
| Microsoft Office | CVE-2020-16949 | Microsoft Outlook Denial of Service Vulnerability | Moderate |
| Microsoft Office | CVE-2020-16947 | Microsoft Outlook Remote Code Execution Vulnerability | Critical |
| Microsoft Office | CVE-2020-16931 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office | CVE-2020-16954 | Microsoft Office Remote Code Execution Vulnerability | Important |
| Microsoft Office | CVE-2020-17003 | Base3D Remote Code Execution Vulnerability | Critical |
| Microsoft Office SharePoint | CVE-2020-16948 | Microsoft SharePoint Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-16953 | Microsoft SharePoint Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-16942 | Microsoft SharePoint Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-16951 | Microsoft SharePoint Remote Code Execution Vulnerability | Critical |
| Microsoft Office SharePoint | CVE-2020-16944 | Microsoft SharePoint Reflective XSS Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-16945 | Microsoft Office SharePoint XSS Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-16946 | Microsoft Office SharePoint XSS Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-16941 | Microsoft SharePoint Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-16950 | Microsoft SharePoint Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-16952 | Microsoft SharePoint Remote Code Execution Vulnerability | Critical |
| Microsoft Windows | CVE-2020-16900 | Windows Event System Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16901 | Windows Kernel Information Disclosure Vulnerability | Important |
| Microsoft Windows | CVE-2020-16899 | Windows TCP/IP Denial of Service Vulnerability | Important |
| Microsoft Windows | CVE-2020-16908 | Windows Setup Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16909 | Windows Error Reporting Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16912 | Windows Backup Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16940 | Windows - User Profile Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16907 | Win32k Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16936 | Windows Backup Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16898 | Windows TCP/IP Remote Code Execution Vulnerability | Critical |
| Microsoft Windows | CVE-2020-16897 | NetBT Information Disclosure Vulnerability | Important |
| Microsoft Windows | CVE-2020-16895 | Windows Error Reporting Manager Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16919 | Windows Enterprise App Management Service Information Disclosure Vulnerability | Important |
| Microsoft Windows | CVE-2020-16921 | Windows Text Services Framework Information Disclosure Vulnerability | Important |
| Microsoft Windows | CVE-2020-16920 | Windows Application Compatibility Client Library Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16972 | Windows Backup Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16877 | Windows Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16876 | Windows Application Compatibility Client Library Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16975 | Windows Backup Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16973 | Windows Backup Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16974 | Windows Backup Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16922 | Windows Spoofing Vulnerability | Important |
| Microsoft Windows | CVE-2020-0764 | Windows Storage Services Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16980 | Windows iSCSI Target Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-1080 | Windows Hyper-V Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16887 | Windows Network Connections Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16885 | Windows Storage VSP Driver Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16924 | Jet Database Engine Remote Code Execution Vulnerability | Important |
| Microsoft Windows | CVE-2020-16976 | Windows Backup Service Elevation of Privilege Vulnerability | Important |
| Microsoft Windows | CVE-2020-16935 | Windows COM Server Elevation of Privilege Vulnerability | Important |
| Microsoft Windows Codecs Library | CVE-2020-16967 | Windows Camera Codec Pack Remote Code Execution Vulnerability | Critical |
| Microsoft Windows Codecs Library | CVE-2020-16968 | Windows Camera Codec Pack Remote Code Execution Vulnerability | Critical |
| PowerShellGet | CVE-2020-16886 | PowerShellGet Module WDAC Security Feature Bypass Vulnerability | Important |
| Visual Studio | CVE-2020-16977 | Visual Studio Code Python Extension Remote Code Execution Vulnerability | Important |
| Windows COM | CVE-2020-16916 | Windows COM Server Elevation of Privilege Vulnerability | Important |
| Windows Error Reporting | CVE-2020-16905 | Windows Error Reporting Elevation of Privilege Vulnerability | Important |
| Windows Hyper-V | CVE-2020-16894 | Windows NAT Remote Code Execution Vulnerability | Important |
| Windows Hyper-V | CVE-2020-1243 | Windows Hyper-V Denial of Service Vulnerability | Important |
| Windows Hyper-V | CVE-2020-16891 | Windows Hyper-V Remote Code Execution Vulnerability | Critical |
| Windows Installer | CVE-2020-16902 | Windows Installer Elevation of Privilege Vulnerability | Important |
| Windows Kernel | CVE-2020-16889 | Windows KernelStream Information Disclosure Vulnerability | Important |
| Windows Kernel | CVE-2020-16892 | Windows Image Elevation of Privilege Vulnerability | Important |
| Windows Kernel | CVE-2020-16913 | Win32k Elevation of Privilege Vulnerability | Important |
| Windows Kernel | CVE-2020-1047 | Windows Hyper-V Elevation of Privilege Vulnerability | Important |
| Windows Kernel | CVE-2020-16910 | Windows Security Feature Bypass Vulnerability | Important |
| Windows Media Player | CVE-2020-16915 | Media Foundation Memory Corruption Vulnerability | Critical |
| Windows RDP | CVE-2020-16863 | Windows Remote Desktop Service Denial of Service Vulnerability | Important |
| Windows RDP | CVE-2020-16927 | Windows Remote Desktop Protocol (RDP) Denial of Service Vulnerability | Important |
| Windows RDP | CVE-2020-16896 | Windows Remote Desktop Protocol (RDP) Information Disclosure Vulnerability | Important |
| Windows Secure Kernel Mode | CVE-2020-16890 | Windows Kernel Elevation of Privilege Vulnerability | Important |
Google’s Keep note-taking app is getting a new feature courtesy of Android 14 that’s a huge time-saver, even if Samsung got there first
There’s a certain balance that needs to be achieved with lock screen functionality. You can’t give away too much because of, well, securit...

-
It’s pretty easy to read your emails while you’re on the go, but responding to those emails takes effort. Smart Reply, available in Inbo...
-
Use Companion Mode with Google Meet for hybrid learning Important: Some features, such as hand raising, require specific Google Workspace...